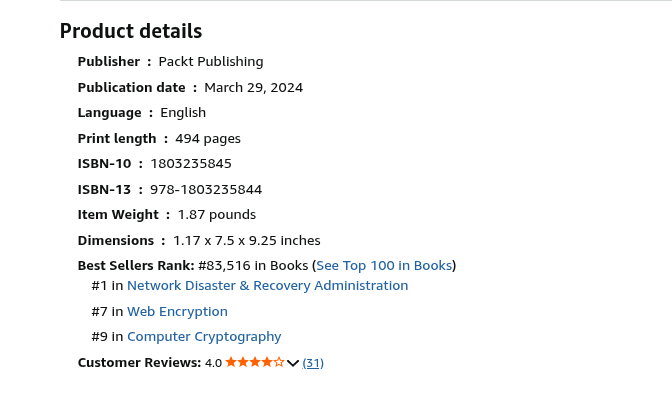
When I first published "The Cybersecurity Architect's Handbook" over a year ago, I hoped it would resonate with cybersecurity professionals looking to advance their careers. What I didn't anticipate was the incredible sustained success the book would achieve—maintaining its position in Amazon's Top 100 across multiple categories for 426 days and counting, including repeatedly claiming the #1 spot in Network Disaster & Recovery Administration.
A Testament to Industry Need
The book's enduring success speaks to a critical gap in the cybersecurity industry: the need for comprehensive guidance on transitioning from technical security roles to strategic architecture positions. Over the past 420 days, thousands of readers have found value in the book's holistic approach to cybersecurity architecture, from foundational concepts to advanced implementation strategies.
Consistent Top 100 Performance Across Key Categories
The sustained performance across Amazon's most competitive cybersecurity categories demonstrates the book's broad appeal and practical value:
- Network Disaster & Recovery Administration: Not just maintaining Top 100 status, but repeatedly achieving #1—a testament to the book's practical approach to business continuity and resilience planning
- Web Encryption: Consistently ranking in the Top 100, reflecting the book's comprehensive coverage of cryptographic principles and implementation strategies
- Computer Cryptography: Maintaining Top 100 status by addressing both theoretical foundations and real-world applications of cryptographic technologies
What's Driving This Sustained Success?
1. Practical, Real-World Focus
Unlike purely academic texts, the handbook bridges the gap between theory and practice. Readers consistently praise the scenario-based examples and lab exercises that help them apply concepts immediately in their work environments.
2. Comprehensive Career Roadmap
The book doesn't just teach technical skills—it provides a complete roadmap for career advancement. From entry-level positions to senior architect roles, it addresses the full journey that cybersecurity professionals need to navigate.
3. Industry-Relevant Content
With chapters covering everything from Zero Trust architecture to cloud-native security patterns, the book stays relevant to current industry challenges and emerging technologies.
4. Community Building
The book has fostered a community of cybersecurity professionals who continue to engage with the content and share their implementation experiences, creating a cycle of continued relevance and discovery.
The #1 Position in Network Disaster & Recovery Administration
Perhaps most gratifying is the book's repeated achievement of the #1 position in Network Disaster & Recovery Administration. This category represents one of the most critical aspects of cybersecurity architecture—ensuring business continuity in the face of threats and disasters.
The book's treatment of Business Continuity Planning (BCP) and Disaster Recovery Planning (DRP) from an architectural perspective has clearly resonated with professionals responsible for organizational resilience.
What This Means for the Cybersecurity Community
The sustained success of "The Cybersecurity Architect's Handbook" reflects several important trends in our industry:
Growing Recognition of Architecture's Importance
More organizations are recognizing that cybersecurity is not just about deploying tools—it requires thoughtful architectural design that aligns with business objectives while maintaining robust security postures.
Demand for Holistic Skill Development
Today's cybersecurity professionals need more than technical expertise. They need to understand business operations, regulatory requirements, risk management, and strategic planning. The book's holistic approach addresses this comprehensive skill requirement.
The Value of Practical Guidance
In an industry often dominated by vendor-specific training and certifications, there's clear demand for vendor-neutral, principle-based guidance that professionals can apply across different technologies and environments.
Looking Forward: Continued Relevance in a Changing Landscape
As we approach the book's second year in publication, its continued success demonstrates that foundational principles of cybersecurity architecture remain constant even as technologies evolve. The book's emphasis on adaptability, business alignment, and strategic thinking continues to serve readers well as they navigate emerging challenges like AI security, quantum cryptography preparation, and evolving regulatory landscapes.
A Personal Reflection
As the author, watching "The Cybersecurity Architect's Handbook" maintain its position in Amazon's top rankings for over 426 days has been both humbling and energizing. Every day, new readers discover the book and begin their journey toward becoming cybersecurity architects. The consistent feedback from readers who have successfully applied the book's principles to advance their careers or improve their organizations' security postures is incredibly rewarding.
The book's success also reinforces my belief that our industry needs more resources that bridge the gap between technical implementation and strategic leadership. Cybersecurity architects play a crucial role in organizational success, and having the right guidance to develop these professionals is essential for our collective security.
Thank You to the Community
The sustained success of "The Cybersecurity Architect's Handbook" wouldn't be possible without the incredible cybersecurity community that has embraced it. From the readers who leave thoughtful reviews to the professionals who recommend it to their colleagues, this community continues to drive the book's success and impact.
To those who have made the handbook part of their professional development journey: thank you for trusting me to guide you on this path. To those considering a move into cybersecurity architecture: I encourage you to join this growing community of professionals who are shaping the future of organizational security.
As we continue beyond day 426, I'm excited to see how the next generation of cybersecurity architects will apply these principles to solve tomorrow's security challenges. The journey continues, and the handbook remains your trusted companion along the way.
If you have not gotten your copy, consider picking one up at Amazon!