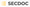As a cybersecurity architect and enthusiast, I've worked extensively with both Pi-hole and AdGuard Home in various environments. In fact I use Pi-hole with unbound DNS for my home environment. Let me share my insights into these two network protection tools, including their logging and monitoring capabilities - a crucial aspect often overlooked in typical comparisons.
The Core Experience
Both solutions excel at their primary task: network-wide ad blocking and DNS filtering. However, their approaches differ significantly in both philosophy and implementation.
Pi-hole: The Classic Defender
Pi-hole follows the Unix philosophy of doing one thing well. It's like a well-oiled machine that's been refined over years of community input. Its command-line first approach might seem intimidating to newcomers, but it provides unparalleled control and automation capabilities.
AdGuard Home: The Modern Guardian
AdGuard Home, in contrast, feels like a premium security appliance. Its polished interface and integrated features make it more accessible to users transitioning from consumer-grade solutions to network-wide protection.
Using Pi-hole or AdGuard Home as Your DHCP Server: Simplifying Network Management
One of the lesser-discussed but powerful features of both Pi-hole and AdGuard Home is their ability to function as DHCP servers. For small networks (single network ex. 172.16.1.1/24), particularly home networks or small offices, this capability can streamline network management and provide enhanced visibility into device activities.
Why Use Your DNS Filter as a DHCP Server?
Before diving into the specifics, let's understand the benefits:
- Centralized management of network assignments
- Better device identification in query logs
- Simplified network configuration
- Enhanced tracking of device activities
- Elimination of potential conflicts with router DHCP
- More detailed network insights
Pi-hole's DHCP Implementation
Pi-hole offers a straightforward DHCP server implementation that can be enabled through the web interface:
- Enabling DHCP
- Access the Pi-hole admin interface
- Navigate to Settings > DHCP
- Enable DHCP server
- Configure your IP range and lease time
- Key Features
- Static IP assignment
- DHCP reservation
- Client hostname tracking
- Customizable lease times
- IPv6 support (optional)
- MAC address tracking
AdGuard Home's DHCP Server
AdGuard Home also provides robust DHCP capabilities:
- Configuration
- Open AdGuard Home dashboard
- Go to Settings > DHCP Settings
- Enable DHCP server
- Define your network parameters
- Notable Features
- Modern interface for DHCP management
- Static lease management
- Dynamic IP assignment
- Client identification
- Gateway configuration
- Network range definition
Setting Up Your DHCP Server
Important Steps for Both Platforms:
- Disable Existing DHCP
- Turn off DHCP on your router
- Ensure no other DHCP servers are active
- Wait for existing leases to expire
- Configure IP Range
- Choose a suitable IP range
- Set appropriate lease times
- Configure DNS settings
- Define gateway information
- Test Configuration
- Connect a new device
- Verify IP assignment
- Check DNS resolution
- Monitor DHCP logs
Best Practices
- Network Planning
- Reserve IPs for critical devices
- Document your IP assignments
- Plan your IP ranges carefully
- Consider future expansion
- Backup Considerations
- Backup DHCP configurations
- Document static assignments
- Keep lease information secure
- Plan for failover scenarios
- Monitoring
- Regular lease table review
- Check for unauthorized devices
- Monitor DHCP performance
- Track IP conflicts
Example Configurations
Pi-hole DHCP Settings:
DHCP Range: 192.168.1.100 - 192.168.1.250
Lease Time: 24 hours
Router (Gateway): 192.168.1.1
Domain Name: local
AdGuard Home DHCP Settings:
Interface: eth0
Gateway IP: 192.168.1.1
Subnet Mask: 255.255.255.0
Range Start: 192.168.1.100
Range End: 192.168.1.250
Lease Duration: 86400 seconds
Troubleshooting Tips
- Common Issues
- IP conflicts
- Lease renewal problems
- DNS resolution failures
- Client connectivity issues
- Resolution Steps
- Check DHCP logs
- Verify network settings
- Release/renew client IPs
- Monitor network traffic
Security Considerations
- Network Protection
- Limit DHCP scope
- Monitor for rogue DHCP servers
- Regular security audits
- Access control implementation
- Best Practices
- Use strong authentication
- Regular configuration backups
- Monitor lease activities
- Document all changes
Using either Pi-hole or AdGuard Home as your DHCP server can significantly simplify network management while providing enhanced visibility into your network activities. Both platforms offer robust DHCP capabilities that, when properly configured, can improve your network's efficiency and security.
The choice between them often comes down to personal preference and specific needs:
- Pi-hole offers a more traditional, straightforward approach
- AdGuard Home provides a more modern, user-friendly interface
Whichever platform you choose, centralizing your DNS filtering and DHCP services can lead to better network management and improved visibility into your network activities.
Remember to plan carefully, document your setup, and maintain regular backups of your DHCP configuration to ensure smooth network operations.
Logging and Monitoring Capabilities
This is where things get interesting, especially for security professionals and network administrators. In the world of network security and DNS filtering, logging capabilities play a crucial role in monitoring and troubleshooting.
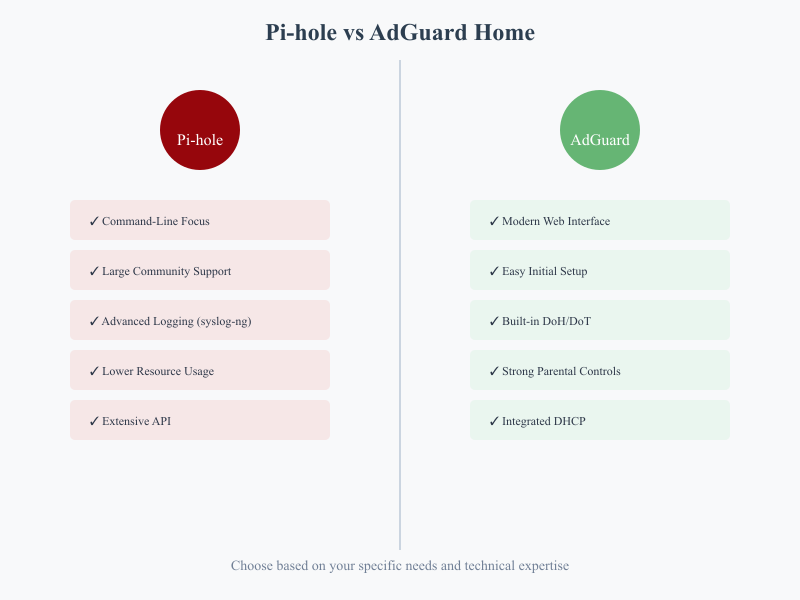
Pi-hole's Logging Architecture
For organizations and individuals serious about network monitoring and security, Pi-hole's approach to logging stands out with its enterprise-ready capabilities. Let's explore how Pi-hole's native logging features provide the flexibility needed in modern security environments.
Native Syslog Integration
Pi-hole was designed with enterprise logging requirements in mind. Out of the box, Pi-hole integrates seamlessly with syslog, making it a natural fit for organizations with existing log management infrastructure. This integration isn't just an afterthought – it's a core feature that reflects Pi-hole's understanding of enterprise needs.
- Native logging to system logs
- Easy integration with syslog-ng/rsyslog
- Granular logging configuration
- JSON logging support
- Query logging with extensive metadata
Comprehensive Logging Options
Pi-hole provides multiple logging streams:
- DNS queries
- FTL (Faster Than Light) daemon logs
- Web interface access logs
- System performance metrics
- Blocking events and statistics
Example syslog-ng configurations for Pi-hole:
Add the file as shown below:
/etc/syslog-ng/conf.d/10-pihole.conf
source s_pihole_log { file("/var/log/pihole.log"); };
destination d_graylog {udp("192.168.1.100" port(2515)); };
log { source(s_pihole_log); destination(d_graylog); };Modify the following file section:
/etc/syslog-ng/syslog-ng.conf
###
# Include all config files in /etc/syslog-ng/conf.d/
###
@include "/etc/syslog-ng/conf.d/*.conf"Or
source s_pihole {
file("/var/log/pihole.log");
file("/var/log/pihole-FTL.log");
};
destination d_siem {
syslog("siem.example.com" transport("tcp")
port(1514)
disk-buffer(
mem-buf-size(10485760)
disk-buf-size(2147483648)
reliable(yes)
)
);
};
log {
source(s_pihole);
destination(d_siem);
};
Integration Benefits
- SIEM Integration
- Direct forwarding to popular SIEM platforms
- Real-time alert configuration
- Correlation with other security events
- Compliance Requirements
- Meets logging requirements for various standards
- Maintains log integrity
- Supports long-term log retention
- Operational Monitoring
- Real-time performance monitoring
- Capacity planning
- Troubleshooting capabilities
Pi-hole's native syslog support and flexible logging architecture make it an excellent choice for environments requiring robust logging capabilities. Whether you're running a small home network or a large enterprise infrastructure, Pi-hole provides the logging tools needed for effective monitoring and security analysis.
The ability to seamlessly integrate with existing logging infrastructure while maintaining detailed DNS query logs makes Pi-hole particularly valuable in security-conscious environments. Its support for standard logging protocols and formats ensures that organizations can maintain visibility into their DNS traffic without compromising on logging capabilities or creating additional complexity in their logging infrastructure.
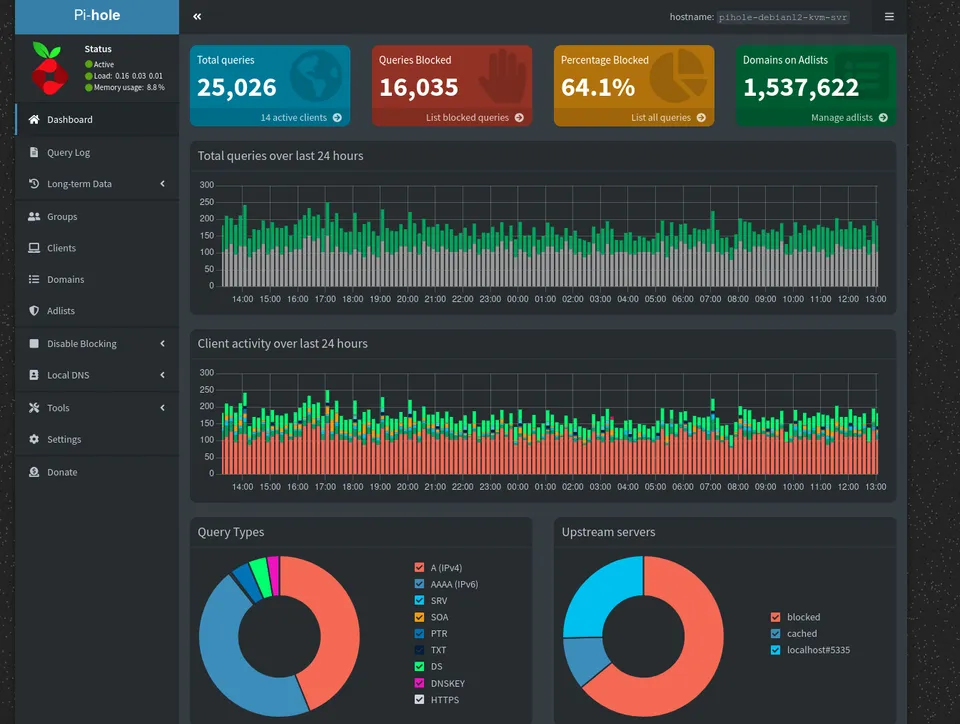
AdGuard Home's Logging Approach
A notable GitHub discussion from 2019 highlighted AdGuard Home's distinct philosophy regarding log management, particularly their decision to avoid implementing syslog support.
The Philosophy of Simplicity
AdGuard Home's development team made a deliberate choice to maintain a focused approach to logging by supporting only their own file format. This decision reflects a broader design philosophy that prioritizes simplicity and reliability over extensive integration options.
The Technical Implementation
Instead of supporting multiple logging destinations, AdGuard Home implemented a straightforward but effective logging solution:
- JSON-formatted query logs
- Support for standard Unix tools (grep, sort)
- Configurable memory buffer for log messages
- Direct file system storage
The Trade-offs
Advantages
- Simplified codebase maintenance
- Reliable, predictable logging behavior
- Easy processing with standard command-line tools
- Direct control over log format and storage
Limitations
- No native integration with centralized logging systems
- Additional configuration required for log forwarding
- Extra steps needed for SIEM integration
- Manual setup needed for real-time log monitoring
The Workaround
While AdGuard Home doesn't directly support syslog or other logging destinations, they've provided a practical alternative. By implementing a configurable buffer size for log messages and using a standard JSON format, they've enabled users to build their own log synchronization solutions using external tools.
Implications for Enterprise Users
For enterprise environments requiring centralized logging:
- Implement file monitoring solutions
- Use log shipping tools like filebeat
- Create custom log forwarding scripts
- Consider third-party log collection agents
Looking Forward
While this approach might seem limiting compared to Pi-hole's native syslog support, it aligns with AdGuard Home's philosophy of maintaining a focused, reliable core functionality. Users requiring advanced logging integration can leverage the JSON log files with standard tools to achieve their desired logging setup.
For security professionals and system administrators, this means planning additional steps for log integration, but also provides flexibility in how logs are processed and forwarded to other systems.
The decision, while potentially controversial, demonstrates AdGuard Home's commitment to maintaining a streamlined, maintainable codebase while still providing the necessary tools for users to implement more complex logging solutions when needed.
- Built-in query logging
- Native JSON logging capabilities
- HTTP API for log access
- Retention configuration
- Direct log export features
Example AdGuard Home logging configuration:
log:
file: "/var/log/adguard.log"
format: json
compress: true
max_backups: 3
max_size: 100
max_age: 7
Integration with Security Tools
Pi-hole
- Native support for syslog forwarding
- Easy integration with:
- Graylog
- Splunk
- ELK Stack
- Custom SIEM solutions
- Extensive API for custom integrations
- Community-developed monitoring solutions
AdGuard Home
- Built-in monitoring features
- RESTful API for integration
- Webhook support for alerts
- Native support for monitoring systems
- Integration with popular monitoring platforms
Real-world Performance
From my experience deploying both solutions in various environments, here's what I've observed:
Pi-hole Strengths:
- More efficient in high-query environments
- Better handling of large blocklists
- More flexible logging options
- Stronger community support for enterprise integrations
- Better documentation for advanced configurations
AdGuard Home Strengths:
- More intuitive monitoring interface
- Better built-in reporting
- Easier initial setup
- More modern security features out of the box
- Better handling of dynamic network environments
Making the Choice
Your decision should be based on several factors:
- Technical Expertise
- Pi-hole for those comfortable with CLI
- AdGuard Home for those preferring GUI management
- Monitoring Requirements
- Pi-hole for complex SIEM integrations
- AdGuard Home for built-in monitoring needs
- Scale
- Pi-hole for larger networks
- AdGuard Home for small to medium deployments
- Security Integration
- Pi-hole for custom security stacks
- AdGuard Home for modern, integrated security features
Final Thoughts
Both solutions are excellent choices for network protection, but they serve slightly different needs. Pi-hole excels in environments requiring extensive customization and integration with existing security infrastructure, while AdGuard Home shines in situations requiring a modern, integrated solution with minimal setup overhead.
For those focused on security monitoring and logging, Pi-hole's mature logging infrastructure and extensive integration options make it a slightly better choice and part of the reason why I use Pi-hole. However, AdGuard Home's modern approach and built-in features might be more appropriate for environments where immediate visibility and ease of use are priorities.
Remember, the best choice depends on your specific needs, technical capabilities, and existing infrastructure. Both tools continue to evolve, and their capabilities grow with each release.