Introduction
Before we dive into the installation process, let's address a common question: How do you pronounce Wazuh?
Wazuh is pronounced "WAH-zoo" - think of it as rhyming with "voodoo" but starting with a "W". This open-source security platform has become a cornerstone of many security operations centers, and knowing how to properly say its name is the first step in joining the community!
The OSSEC Legacy: Understanding Wazuh's Foundation
From OSSEC to Wazuh: An Evolution Story
Wazuh is built upon the solid foundation of OSSEC (Open Source HIDS SECurity), one of the world's most widely used Host-based Intrusion Detection Systems (HIDS). Understanding this heritage is crucial to appreciating Wazuh's capabilities and architecture.

OSSEC: The Pioneer (2004-2019)
- Created by Daniel Cid in 2004
- Became the de facto standard for open-source HIDS
- Acquired by Trend Micro in 2009
- Development slowed significantly after 2017
- Last stable release: OSSEC 3.6.0 (2019)
Why Wazuh Was Born (2015) In 2015, as OSSEC development stagnated, the Wazuh team (originally OSSEC contributors) forked the project to:
- Add modern security capabilities
- Improve scalability and performance
- Provide better integration with modern tools
- Maintain active development and community support
- Add enterprise features while keeping it open source
What Wazuh Inherited from OSSEC
Core Architecture Elements
- Agent-Manager Architecture: The fundamental client-server model
- Rule-Based Detection: The powerful XML-based rule engine
- Log Analysis Engine: Real-time log processing capabilities
- File Integrity Monitoring: Detecting changes to critical files
- Rootkit Detection: System-level threat detection
- Active Response: Automated threat mitigation
Directory Structure (Still reflects OSSEC heritage)
/var/ossec/ # Main Wazuh directory (kept for compatibility)
├── bin/ # Binaries and executables
├── etc/ # Configuration files
├── logs/ # Log files
├── queue/ # Event queues
├── ruleset/ # Rules and decoders
└── active-response/ # Response scripts
How Wazuh Enhanced OSSEC
Major Improvements and Additions
- RESTful API
- OSSEC: No API, only command-line tools
- Wazuh: Full RESTful API for integration and automation
- Wazuh Dashboard (formerly Kibana App)
- OSSEC: Limited web UI (OSSEC-WUI)
- Wazuh: Full-featured dashboard with visualizations
- Elasticsearch/OpenSearch Integration
- OSSEC: File-based storage only
- Wazuh: Scalable indexing and searching
- Cloud and Container Support
- OSSEC: Traditional infrastructure focus
- Wazuh: Native AWS, Azure, GCP, Docker, and Kubernetes monitoring
- Regulatory Compliance
- OSSEC: Basic compliance features
- Wazuh: Comprehensive compliance modules (PCI DSS, GDPR, HIPAA)
- Vulnerability Detection
- OSSEC: Not included
- Wazuh: Integrated vulnerability scanning
- MITRE ATT&CK Framework
- OSSEC: No framework mapping
- Wazuh: Full MITRE ATT&CK integration
OSSEC to Wazuh Migration Path
For organizations still running OSSEC, Wazuh provides a smooth migration path:
Compatibility Features
- Wazuh agents are backward compatible with OSSEC managers (up to OSSEC 3.x)
- OSSEC agents can connect to Wazuh managers
- OSSEC rules and decoders work in Wazuh with minor modifications
- Configuration files maintain similar structure
Migration Steps
# 1. Backup OSSEC configuration
tar -czf ossec-backup.tar.gz /var/ossec/etc/ /var/ossec/rules/ /var/ossec/decoders/
# 2. Install Wazuh manager (replaces OSSEC manager)
# Follow the installation steps in this guide
# 3. Migrate custom rules and decoders
cp /backup/ossec/rules/local_rules.xml /var/ossec/etc/rules/
cp /backup/ossec/decoders/local_decoder.xml /var/ossec/etc/decoders/
# 4. Update agent configuration to point to new Wazuh manager
# Agents will automatically upgrade protocol
OSSEC Commands Still in Wazuh
Many familiar OSSEC commands remain in Wazuh (with enhancements):
# Classic OSSEC commands that still work
/var/ossec/bin/ossec-control start|stop|status # Now wazuh-control
/var/ossec/bin/manage_agents # Agent management
/var/ossec/bin/ossec-logtest # Now wazuh-logtest
/var/ossec/bin/agent_control # Agent information
/var/ossec/bin/syscheck_control # FIM management
/var/ossec/bin/rootcheck_control # Rootkit detection
# New Wazuh-specific commands
/var/ossec/bin/wazuh-clusterd # Cluster management
/var/ossec/bin/wazuh-apid # API daemon
/var/ossec/bin/wazuh-modulesd # Module manager
Why Choose Wazuh Over OSSEC Today
- Active Development: Wazuh has regular releases; OSSEC development has ceased
- Modern Architecture: API-first design, microservices ready
- Cloud Native: Built for modern infrastructure
- Community: Larger, more active community
- Enterprise Features: While remaining open source
- Better Documentation: Comprehensive, updated documentation
- Professional Support: Available from Wazuh Inc.
What is Wazuh? A Deep Dive into XDR, SIEM, and Compliance
Wazuh as an XDR (Extended Detection and Response) Platform
Wazuh has evolved beyond traditional security monitoring to become a comprehensive XDR platform. Unlike conventional security tools that operate in silos, Wazuh provides:
1. Unified Visibility Across All Vectors
- Endpoint Detection: Monitors file integrity, registry changes, running processes, and network connections
- Network Security: Analyzes network traffic patterns and detects anomalies
- Cloud Workload Protection: Native integrations with AWS, Azure, GCP, and container platforms
- Application Security: Monitors web server logs, database activity, and application behavior
2. Advanced Threat Detection Capabilities
- Behavioral Analysis: Establishes baselines and detects deviations indicating potential threats
- MITRE ATT&CK Mapping: Automatically maps detected activities to MITRE ATT&CK techniques
- Threat Intelligence Integration: Incorporates threat feeds to identify known malicious indicators
- Machine Learning: Uses statistical analysis to identify anomalies and zero-day threats
3. Automated Response and Orchestration
- Active Response: Automatically blocks IPs, kills processes, or quarantines files
- Integration with SOAR: APIs enable integration with Security Orchestration platforms
- Custom Response Scripts: Create tailored responses for your environment
- Rollback Capabilities: Undo automated actions if false positives occur
Wazuh as a Next-Generation SIEM
As a Security Information and Event Management system, Wazuh excels in several areas:
1. Comprehensive Log Collection and Analysis
- Multi-Source Integration: Collects logs from 100+ different sources out-of-the-box
- Real-time Analysis: Processes millions of events per second with minimal latency
- Custom Decoders: Create parsers for proprietary applications
- Correlation Engine: Links related events across different sources
2. Advanced Analytics and Detection
Example: Wazuh can correlate:
- Failed SSH login attempts (auth.log)
- Followed by successful VPN connection (vpn.log)
- Unusual data transfer volumes (netflow)
- New scheduled task creation (Windows Event Log)
= Potential insider threat or compromised credentials
3. Scalability and Performance
- Horizontal Scaling: Add more nodes as your environment grows
- Efficient Storage: Compressed storage with configurable retention policies
- Distributed Architecture: Process events close to their source
- Load Balancing: Distribute processing across multiple managers
4. Rich Visualization and Reporting
- Pre-built Dashboards: 50+ dashboards for different use cases
- Custom Visualizations: Create specific views for your needs
- Executive Reports: Automated PDF generation for management
- Real-time Alerting: Multiple notification channels (email, Slack, PagerDuty)
Wazuh as a Compliance Monitoring Powerhouse
Wazuh provides extensive compliance monitoring capabilities across major frameworks:
1. Regulatory Compliance Coverage
PCI DSS (Payment Card Industry Data Security Standard)
- Requirement 10: Tracks and monitors all access to network resources and cardholder data
- Requirement 11.5: File integrity monitoring for critical system files
- Requirement 2.2: Identifies insecure services and configurations
- Pre-built reports for PCI DSS compliance audits
GDPR (General Data Protection Regulation)
- Article 32: Monitors encryption status and data protection measures
- Article 33: Breach detection and notification capabilities
- Article 25: Privacy by design through configuration assessment
- Data classification and access monitoring
HIPAA (Health Insurance Portability and Accountability Act)
- Security Rule 164.312: Access control and audit logs
- 164.308: Administrative safeguards monitoring
- 164.310: Physical safeguards tracking
- PHI access monitoring and alerting
SOC 2 (Service Organization Control 2)
- Continuous monitoring of security controls
- Change detection and management
- Access control verification
- Availability and processing integrity checks
2. Security Benchmarks and Frameworks
- CIS (Center for Internet Security) Benchmarks: Automated assessment against CIS controls
- NIST Cybersecurity Framework: Maps controls to NIST categories
- ISO 27001/27002: Information security management monitoring
- MITRE ATT&CK: Threat detection mapped to adversary techniques
3. Compliance Monitoring Features
Configuration Assessment
# Example: CIS Benchmark Check
<policy>
<name>CIS: Ensure password complexity is configured</name>
<condition>all</condition>
<rules>
<rule>
<type>PASSWORD_POLICY</type>
<check>
<MinimumPasswordLength>14</MinimumPasswordLength>
<PasswordComplexity>Enabled</PasswordComplexity>
</check>
</rule>
</rules>
</policy>
Automated Compliance Reporting
- Scheduled compliance scans
- Trend analysis over time
- Gap analysis and remediation tracking
- Evidence collection for audits
Policy Enforcement
- Real-time detection of non-compliant changes
- Automated remediation options
- Approval workflows for exceptions
- Compliance score tracking
Use Case Examples
1. Financial Services - XDR Implementation A major bank uses Wazuh to:
- Monitor 50,000 endpoints for malware and insider threats
- Correlate transaction anomalies with system behavior
- Automate incident response for common threats
- Maintain PCI DSS compliance across all payment systems
2. Healthcare Provider - SIEM Deployment A hospital network leverages Wazuh for:
- Centralized logging from medical devices and IT systems
- HIPAA compliance monitoring and reporting
- Detection of unauthorized access to patient records
- Integration with their incident response platform
3. E-commerce Platform - Compliance Monitoring An online retailer uses Wazuh to:
- Maintain PCI DSS compliance for payment processing
- Monitor GDPR compliance for customer data handling
- Track configuration changes across their infrastructure
- Generate monthly compliance reports for stakeholders
In this comprehensive guide, we'll walk through two deployment scenarios:
- All-in-one installation - Perfect for testing, small environments, or proof-of-concept deployments
- Distributed installation - Ideal for production environments requiring scalability and high availability
Understanding Wazuh Architecture
Before we dive into the installation process, it's crucial to understand Wazuh's three core components and their OSSEC heritage:
- Wazuh Manager (Server): The brain of the operation, processing data from agents and generating alerts. Built on OSSEC's ossec-analysisd and ossec-remoted
- Wazuh Indexer: Based on OpenSearch, stores and indexes all the security data (replacing OSSEC's file-based storage)
- Wazuh Dashboard: The web interface for visualization and management (replacing the limited OSSEC-WUI)
Prerequisites and System Requirements
Minimum Hardware Requirements
All-in-One Deployment:
- CPU: 4 cores
- RAM: 8 GB
- Storage: 50 GB available disk space
Distributed Deployment (per component):
- Wazuh Manager: 2 cores, 4 GB RAM, 50 GB disk
- Wazuh Indexer: 4 cores, 8 GB RAM, 100 GB disk
- Wazuh Dashboard: 2 cores, 4 GB RAM, 50 GB disk
Supported Operating Systems:
- Ubuntu 20.04/22.04 LTS
- CentOS 7/8
- Red Hat Enterprise Linux 7/8/9
- Amazon Linux 2
Network Requirements:
- Ports to open between components:
- 1514/TCP and 1514/UDP (agent communication)
- 1515/TCP (agent enrollment)
- 1516/TCP (cluster communication)
- 9200/TCP (Wazuh indexer)
- 5601/TCP (Wazuh dashboard)
- 55000/TCP (Wazuh API)
Part 1: All-in-One Installation
This method installs all components on a single server - perfect for getting started quickly.
Step 1: Prepare Your System
# Update your system
sudo apt update && sudo apt upgrade -y # For Ubuntu/Debian
# OR
sudo yum update -y # For CentOS/RHEL
# Install required packages
sudo apt install curl apt-transport-https software-properties-common lsb-release -y # Ubuntu/Debian
# OR
sudo yum install curl yum-utils -y # CentOS/RHEL
Step 2: Download and Run the Installation Assistant
# Download the installation assistant
curl -sO https://packages.wazuh.com/4.8/wazuh-install.sh
# Download the configuration file
curl -sO https://packages.wazuh.com/4.8/config.yml
Step 3: Run the Installation
# Make the script executable
chmod +x wazuh-install.sh
# Run the installation (this will take 5-15 minutes)
sudo bash wazuh-install.sh --generate-config-files
The installer will:
- Generate SSL certificates
- Install all three components
- Configure them to work together
- Start all services
- Maintain OSSEC directory structure for compatibility
Note: The installation preserves the /var/ossec/ directory structure from OSSEC for backward compatibility, even though the product is now Wazuh.
Step 4: Access Your Wazuh Installation
Once installation completes, you'll see output similar to:
INFO: --- Summary ---
INFO: You can access the web interface https://<your-server-ip>
User: admin
Password: <auto-generated-password>
INFO: Installation finished.
Save these credentials! You'll need them to access the dashboard.
Step 5: Verify Installation
# Check service status
sudo systemctl status wazuh-manager
sudo systemctl status wazuh-indexer
sudo systemctl status wazuh-dashboard
# Test API access
curl -k -u admin:<your-password> https://localhost:55000/security/user/authenticate
# Check OSSEC/Wazuh processes
ps aux | grep ossec
# You'll see processes like ossec-analysisd, ossec-syscheckd, etc.
Understanding the OSSEC Legacy in Your Installation
After installation, you'll notice several OSSEC references:
- Directory Structure: Main directory is still
/var/ossec/ - Process Names: Many processes retain "ossec" prefix
- Configuration Files: Similar XML structure to OSSEC
- Log Files: Located in
/var/ossec/logs/ - User/Group: Runs as
ossecuser and group
This is intentional - Wazuh maintains compatibility while extending functionality.
Part 2: Distributed Installation
For production environments, separating components across multiple servers provides better performance and reliability.
Architecture Overview
In my deployment I have configured the following:
- Server 1: Wazuh Manager (192.168.37.11)
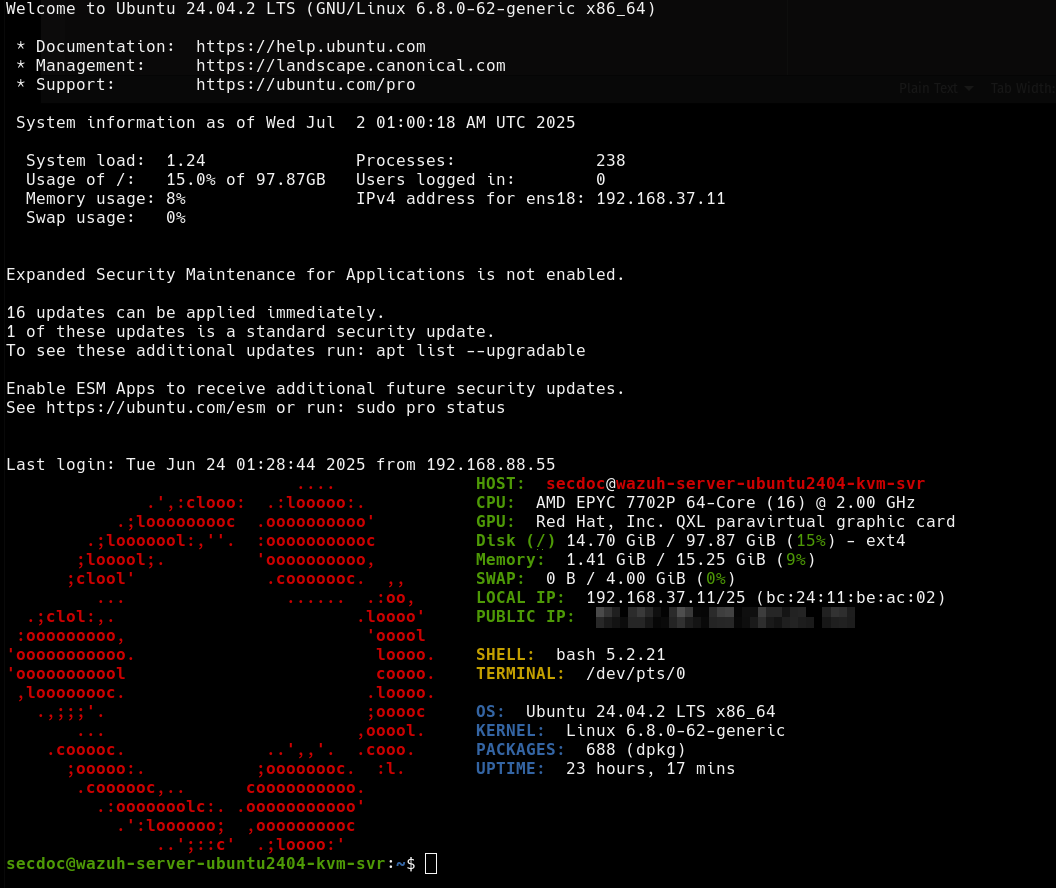
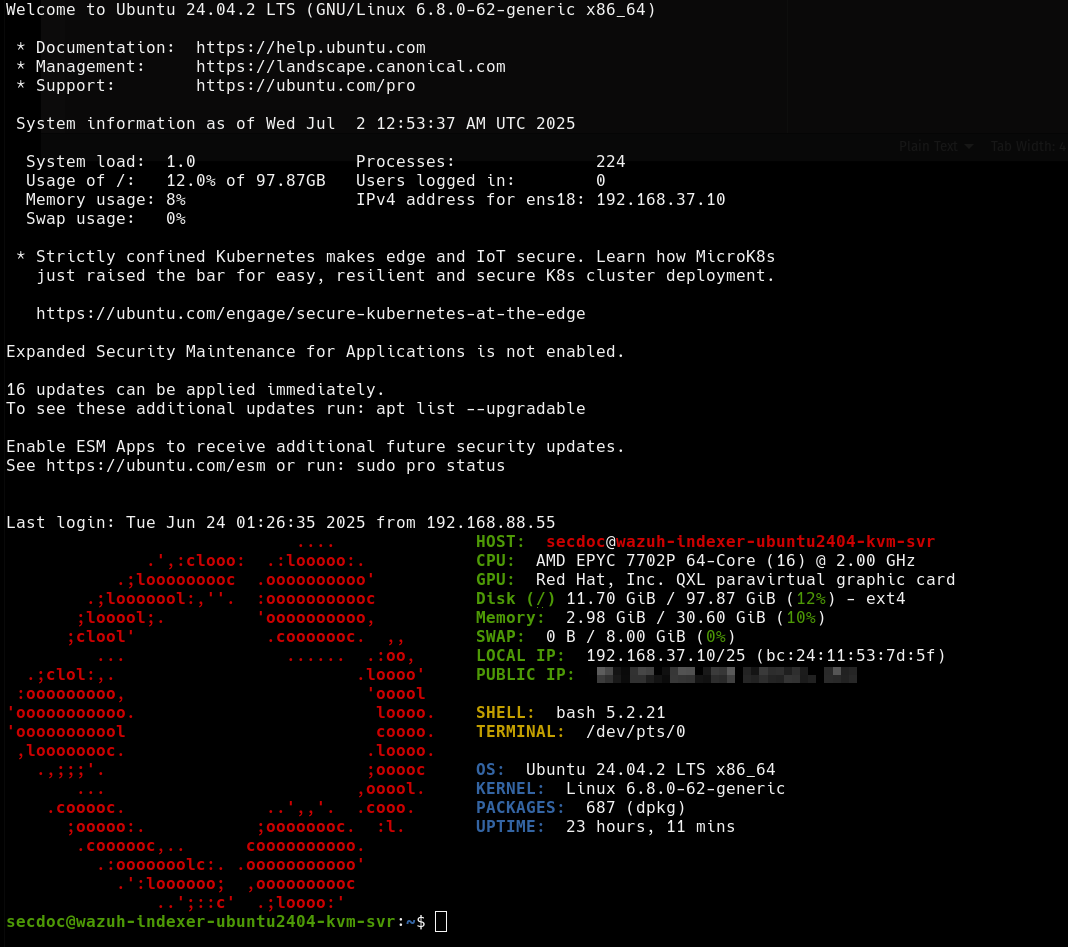
- Server 2: Wazuh Indexer (192.168.37.10)
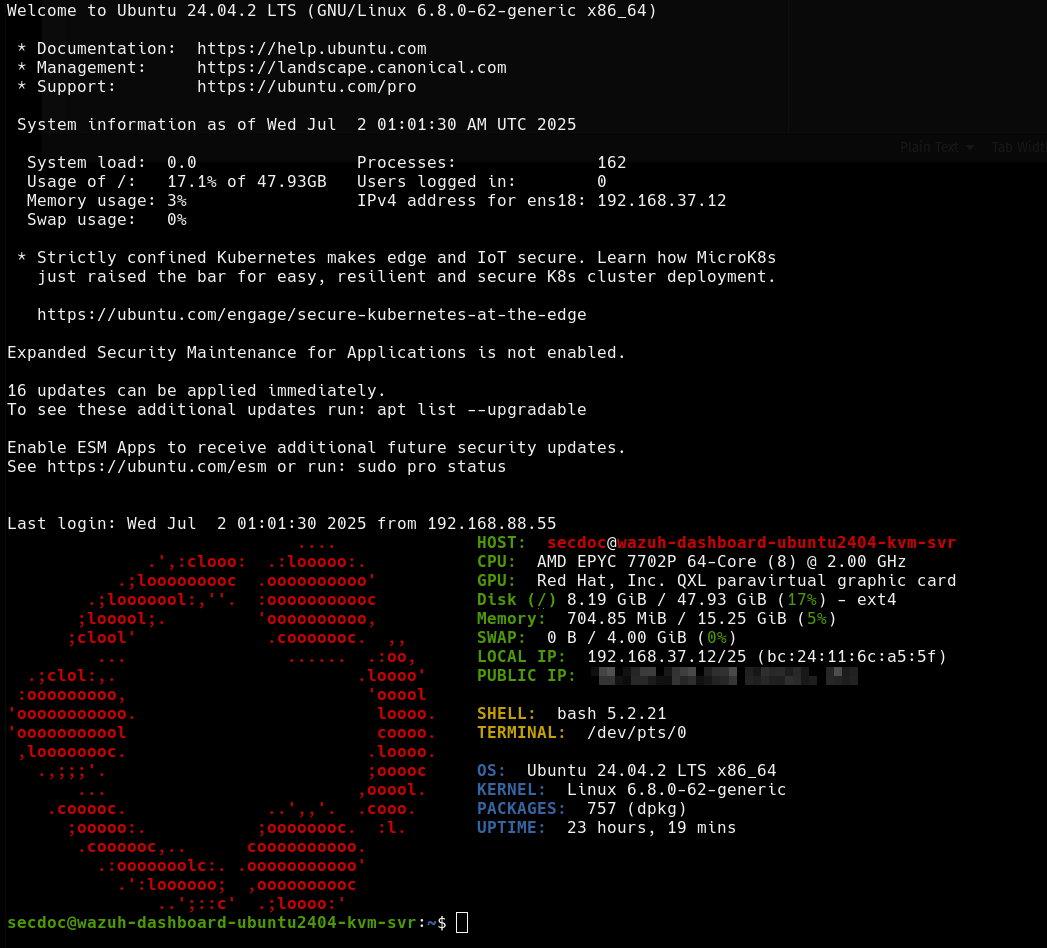
- Server 3: Wazuh Dashboard (192.168.37.12)
Step 1: Generate Certificates and Configuration
On your first server (Manager):
# Download installation files
curl -sO https://packages.wazuh.com/4.8/wazuh-install.sh
curl -sO https://packages.wazuh.com/4.8/config.yml
# Edit config.yml to define your infrastructure
sudo nano config.yml
Update the config.yml with your server details:
nodes:
# Wazuh indexer nodes
indexer:
- name: indexer-1
ip: 192.168.37.10
# Wazuh server nodes
server:
- name: server-1
ip: 192.168.37.11
# Wazuh dashboard nodes
dashboard:
- name: dashboard-1
ip: 192.168.37.12
Generate the certificates:
sudo bash wazuh-install.sh --generate-config-files
This creates a wazuh-install-files.tar file containing certificates and passwords.
Step 2: Install Wazuh Indexer (Server 2)
Copy the tar file to your indexer server, then:
# Extract certificates
sudo tar -xf wazuh-install-files.tar
# Install Wazuh indexer
sudo bash wazuh-install.sh --wazuh-indexer indexer-1
# Start and enable the service
sudo systemctl daemon-reload
sudo systemctl enable wazuh-indexer
sudo systemctl start wazuh-indexer
Verify the installation:
# Check cluster health
curl -k -u admin:<password> https://192.168.37.10:9200/_cat/health?v
Step 3: Install Wazuh Manager (Server 1)
On your manager server:
# Extract certificates
sudo tar -xf wazuh-install-files.tar
# Install Wazuh manager
sudo bash wazuh-install.sh --wazuh-server server-1
# Start and enable services
sudo systemctl daemon-reload
sudo systemctl enable wazuh-manager
sudo systemctl start wazuh-manager
Verify the installation:
# Check manager status
sudo systemctl status wazuh-manager
# Test API
curl -k -u wazuh-wui:<api-password> https://192.168.37.11:55000/security/user/authenticate
Step 4: Install Wazuh Dashboard (Server 3)
Copy the tar file to your dashboard server:
# Extract certificates
sudo tar -xf wazuh-install-files.tar
# Install Wazuh dashboard
sudo bash wazuh-install.sh --wazuh-dashboard dashboard-1
# Start and enable the service
sudo systemctl daemon-reload
sudo systemctl enable wazuh-dashboard
sudo systemctl start wazuh-dashboard
Step 5: Initialize the Cluster
After all components are installed, initialize the cluster:
# Run on any server with the installation files
sudo bash wazuh-install.sh --start-cluster
Post-Installation Configuration
1. Change Default Passwords
For security, immediately change default passwords:
# Change indexer admin password
curl -k -X PUT "https://192.168.37.10:9200/_plugins/_security/api/internalusers/admin" \
-u admin:oldpassword \
-H "Content-Type: application/json" \
-d '{
"password": "NewSecurePassword123!"
}'
2. Configure Firewall Rules
For Ubuntu/Debian with UFW:
# Wazuh Manager
sudo ufw allow 1514/tcp
sudo ufw allow 1514/udp
sudo ufw allow 1515/tcp
sudo ufw allow 55000/tcp
# Wazuh Indexer
sudo ufw allow 9200/tcp
# Wazuh Dashboard
sudo ufw allow 5601/tcp
3. Enable HTTPS/TLS
The installation assistant automatically configures TLS, but verify:
# Check certificate expiration
openssl x509 -enddate -noout -in /etc/wazuh-indexer/certs/indexer.pem
4. Configure Email Notifications
Edit /var/ossec/etc/ossec.conf on the manager:
<ossec_config>
<global>
<email_notification>yes</email_notification>
<smtp_server>smtp.example.com</smtp_server>
<email_from>[email protected]</email_from>
<email_to>[email protected]</email_to>
</global>
</ossec_config>
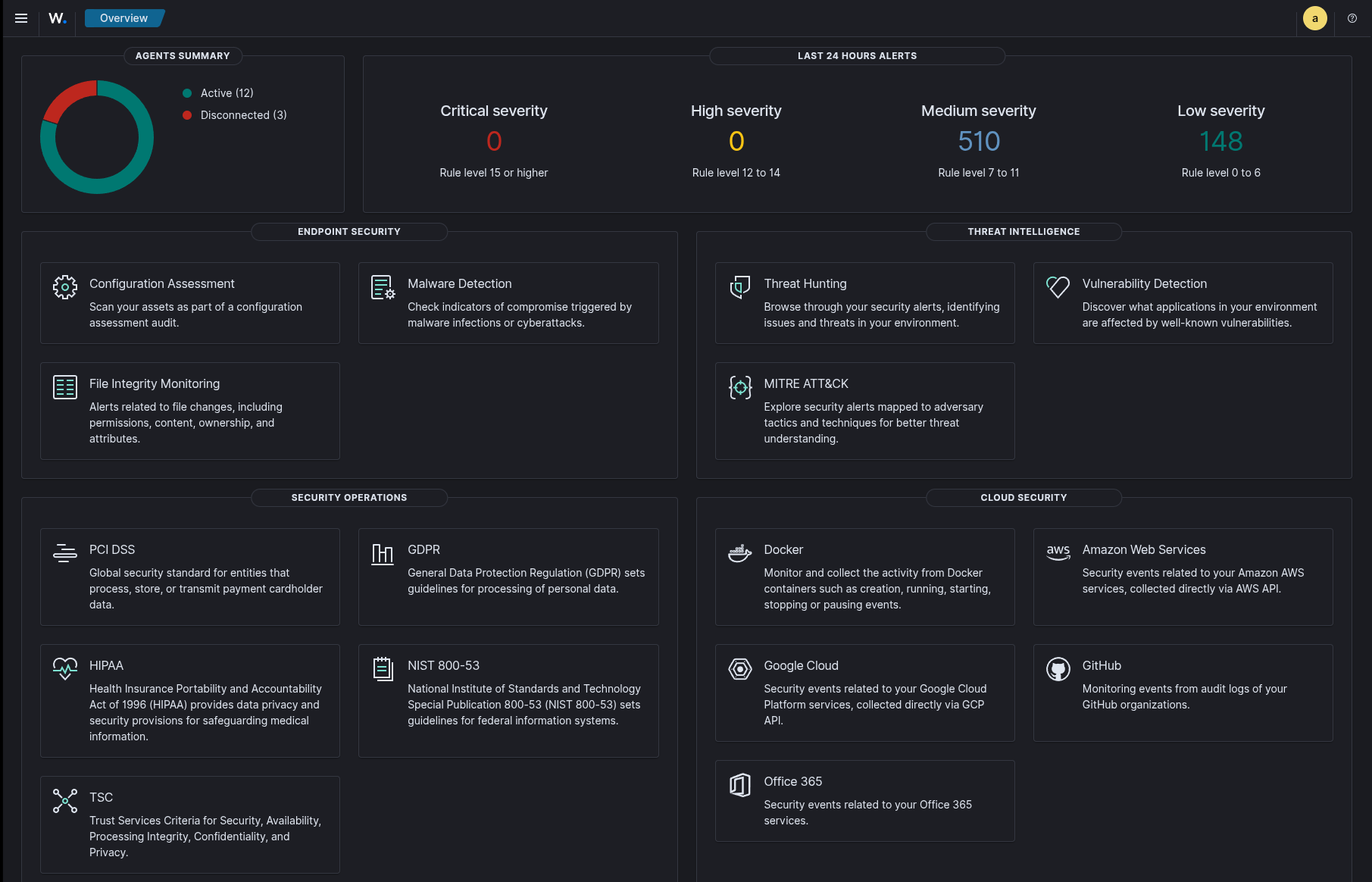
Configuring Wazuh for XDR, SIEM, and Compliance
Setting Up XDR Capabilities
1. Enable Threat Intelligence Integration
<!-- In /var/ossec/etc/ossec.conf -->
<ossec_config>
<ruleset>
<!-- AlienVault OTX Integration -->
<list>etc/lists/alienvault</list>
<!-- AbuseIPDB Integration -->
<list>etc/lists/abuseipdb</list>
<!-- Custom threat feeds -->
<list>etc/lists/custom-threats</list>
</ruleset>
</ossec_config>
2. Configure MITRE ATT&CK Mapping
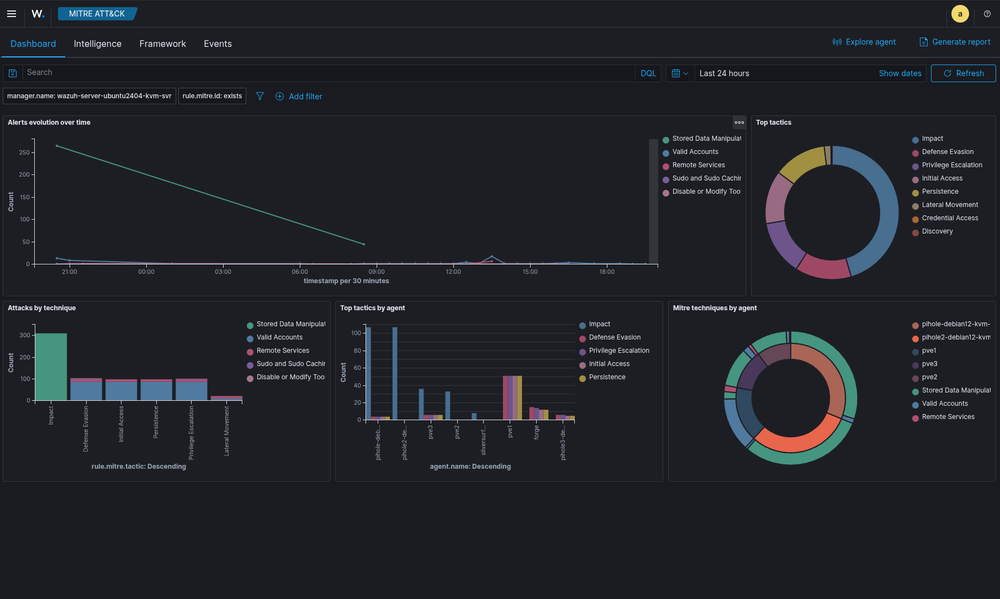
# Enable MITRE rules
cd /var/ossec/ruleset/rules
sudo wget https://raw.githubusercontent.com/wazuh/wazuh/master/ruleset/rules/0015-mitre_rules.xml
3. Set Up Active Response for XDR
<ossec_config>
<active-response>
<n>firewall-block</n>
<executable>firewall-drop</executable>
<level>10</level>
<timeout>600</timeout>
</active-response>
<active-response>
<n>isolate-endpoint</n>
<executable>isolate.sh</executable>
<level>12</level>
<rules_id>100100,100101</rules_id>
</active-response>
</ossec_config>
Configuring SIEM Features
1. Enable Advanced Log Collection
<!-- Collect Windows Event Logs -->
<ossec_config>
<localfile>
<location>Security</location>
<log_format>eventchannel</log_format>
<query>Event/System[EventID != 5145 and EventID != 5156]</query>
</localfile>
<!-- Collect Linux audit logs -->
<localfile>
<location>/var/log/audit/audit.log</location>
<log_format>audit</log_format>
</localfile>
<!-- Collect application logs -->
<localfile>
<location>/var/log/nginx/access.log</location>
<log_format>apache</log_format>
</localfile>
</ossec_config>
2. Create Custom Correlation Rules
<!-- Create /var/ossec/etc/rules/custom_correlation.xml -->
<group name="correlation,">
<!-- Detect brute force followed by successful login -->
<rule id="100200" level="10" frequency="5" timeframe="120">
<if_matched_sid>5710</if_matched_sid>
<description>Multiple authentication failures followed by success</description>
<n>attack,brute_force</n>
</rule>
<!-- Detect data exfiltration -->
<rule id="100201" level="12">
<if_sid>80790</if_sid>
<match>bytes_sent > 1000000</match>
<time>10pm - 6am</time>
<description>Large data transfer during off-hours</description>
<n>attack,exfiltration</n>
</rule>
</group>
Setting Up Compliance Monitoring
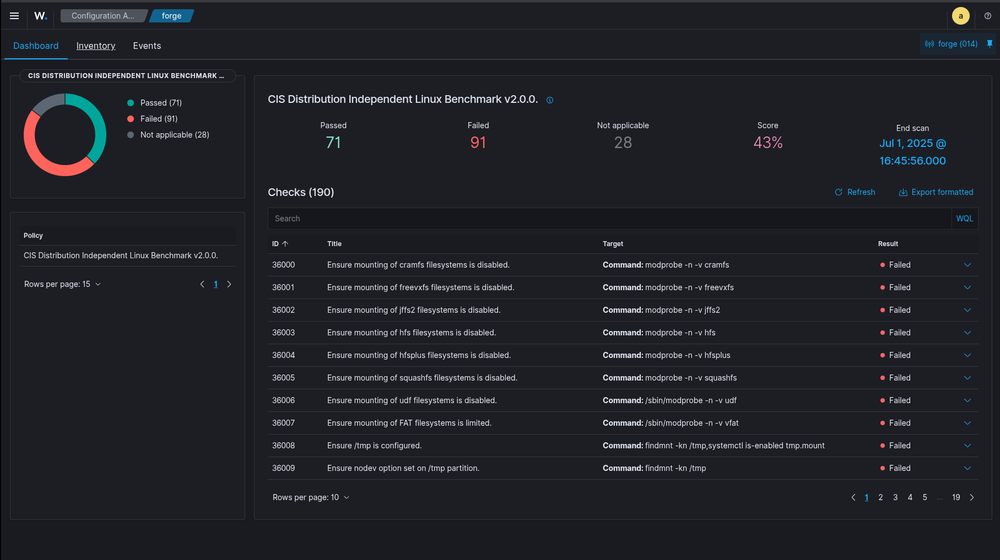
1. Enable CIS Benchmark Scanning
# Create /var/ossec/etc/shared/default/cis_benchmark.yml
n: "CIS Benchmark for Ubuntu 22.04"
requirements:
title: "CIS Ubuntu Linux 22.04 LTS Benchmark"
description: "Center for Internet Security Benchmark"
checks:
- id: 5000
title: "Ensure mounting of cramfs filesystems is disabled"
condition: all
rules:
- 'f:/etc/modprobe.d/cramfs.conf -> r:^install cramfs /bin/true'
- id: 5001
title: "Ensure permissions on /etc/passwd are configured"
condition: all
rules:
- 'c:stat -L /etc/passwd -> r:-rw-r--r--'
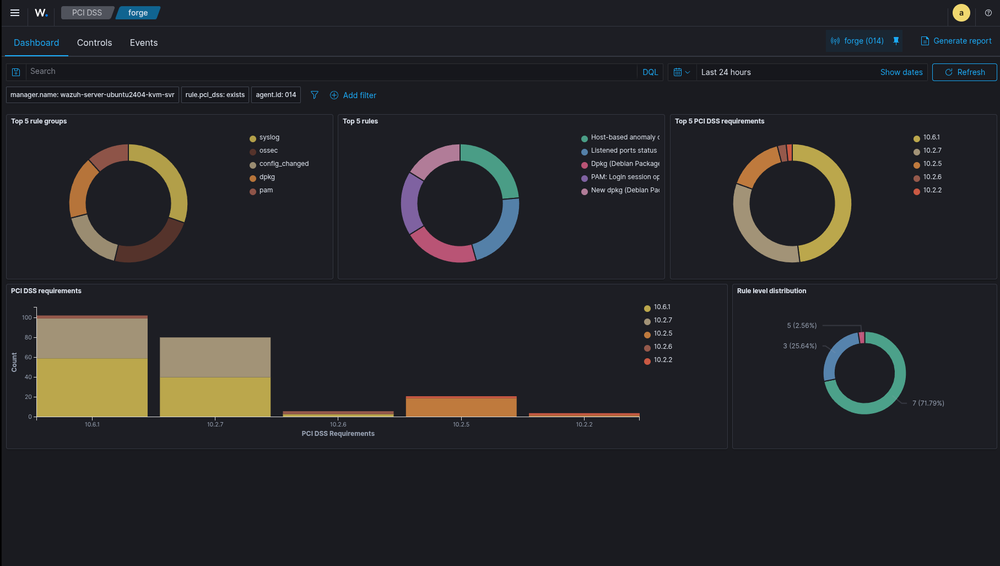
2. Configure PCI DSS Monitoring
<!-- Enable PCI DSS rules -->
<ossec_config>
<ruleset>
<decoder_dir>ruleset/decoders</decoder_dir>
<rule_dir>ruleset/rules</rule_dir>
<rule_exclude>0215-policy_rules.xml</rule_exclude>
<list>etc/lists/audit-keys</list>
<!-- PCI DSS specific rules -->
<rule_include>0350-pci_dss_rules.xml</rule_include>
</ruleset>
<!-- File integrity monitoring for PCI -->
<syscheck>
<frequency>43200</frequency>
<directories check_all="yes" report_changes="yes" realtime="yes">
/etc,/usr/bin,/usr/sbin,/bin,/sbin
</directories>
<!-- PCI DSS 11.5 requirement -->
<directories check_all="yes" report_changes="yes" tag="PCI-DSS-11.5">
/var/www/html,/etc/httpd/conf
</directories>
</syscheck>
</ossec_config>
3. Enable GDPR Compliance Checks
<!-- GDPR monitoring configuration -->
<ossec_config>
<!-- Monitor personal data access -->
<localfile>
<location>/var/log/application/access.log</location>
<log_format>json</log_format>
<label key="gdpr">personal_data_access</label>
</localfile>
<!-- Data retention policies -->
<global>
<logall_json>yes</logall_json>
<jsonout_output>yes</jsonout_output>
<alerts_log>yes</alerts_log>
<stats>4w</stats> <!-- 4 weeks retention -->
</global>
</ossec_config>
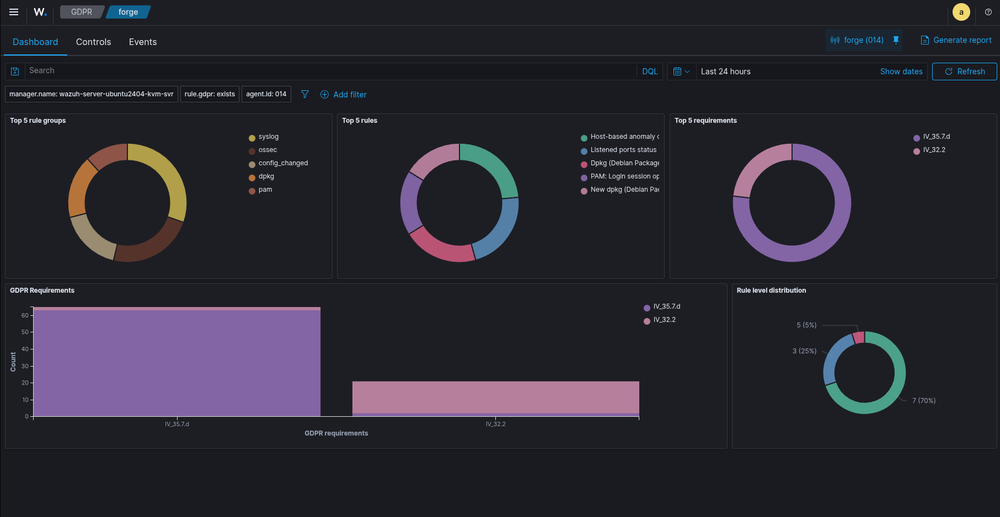
Creating Compliance Dashboards
1. Access Wazuh Dashboard Navigate to your Wazuh dashboard and go to Management > Stack Management > Saved Objects
2. Import Compliance Dashboards
# Download compliance dashboards
wget https://raw.githubusercontent.com/wazuh/wazuh-kibana-app/master/dashboards/compliance/pci-dss.json
wget https://raw.githubusercontent.com/wazuh/wazuh-kibana-app/master/dashboards/compliance/gdpr.json
wget https://raw.githubusercontent.com/wazuh/wazuh-kibana-app/master/dashboards/compliance/hipaa.json
# Import via API
curl -X POST "https://localhost:5601/api/saved_objects/_import" \
-H "kbn-xsrf: true" \
-H "securitytenant: global" \
-F [email protected]
Installing Wazuh Agents
Once your infrastructure is ready, install agents on the systems you want to monitor:
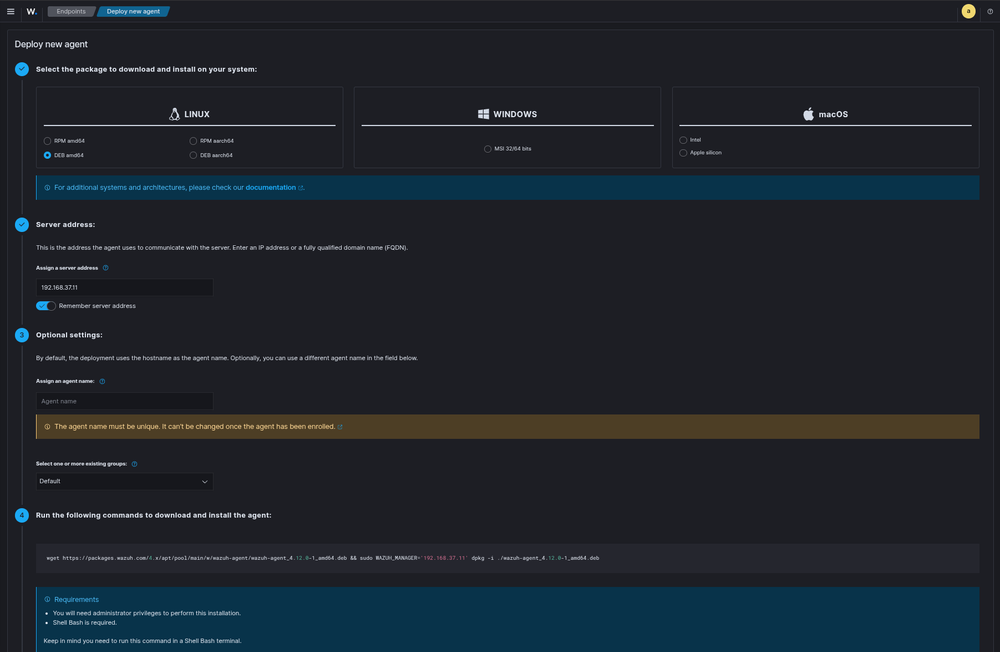
Linux Agent Installation
# Add Wazuh repository
curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | apt-key add -
echo "deb https://packages.wazuh.com/4.x/apt/ stable main" | tee /etc/apt/sources.list.d/wazuh.list
# Install agent
apt update
apt install wazuh-agent
# Configure agent to connect to manager
sudo nano /var/ossec/etc/ossec.conf
# Update <server-ip> with your manager's IP
# Start agent
sudo systemctl start wazuh-agent
sudo systemctl enable wazuh-agent
Windows Agent Installation
- Download the Windows installer from: https://packages.wazuh.com/4.x/windows/
- Run the installer as Administrator
- Enter your Wazuh manager IP during installation
- Start the agent service
Troubleshooting Common Issues
Issue 1: Cannot Access Dashboard
# Check if service is running
sudo systemctl status wazuh-dashboard
# Check logs
sudo tail -f /usr/share/wazuh-dashboard/logs/wazuh-dashboard.log
# Verify connectivity to indexer
curl -k https://192.168.37.10:9200
Issue 2: Agents Not Connecting
# On manager, check if port is listening
sudo netstat -tulpn | grep 1514
# Check manager logs (note the OSSEC path)
sudo tail -f /var/ossec/logs/ossec.log
# On agent, test connectivity
telnet <manager-ip> 1514
Issue 3: High Memory Usage
For indexer memory issues, adjust JVM heap size:
# Edit JVM options
sudo nano /etc/wazuh-indexer/jvm.options
# Set heap size (50% of available RAM)
-Xms4g
-Xmx4g
# Restart indexer
sudo systemctl restart wazuh-indexer
Issue 4: OSSEC to Wazuh Migration Issues
If migrating from OSSEC:
# Check rule compatibility
/var/ossec/bin/wazuh-logtest < /var/log/messages
# Verify custom rules loaded
grep "local_rules" /var/ossec/logs/ossec.log
# Test decoder compatibility
/var/ossec/bin/wazuh-logtest -v
Performance Optimization Tips
1. Indexer Optimization
# Increase file descriptors
echo "wazuh-indexer soft nofile 65536" >> /etc/security/limits.conf
echo "wazuh-indexer hard nofile 65536" >> /etc/security/limits.conf
2. Manager Optimization
For high-volume environments, tune the analysis engine:
<!-- In /var/ossec/etc/ossec.conf -->
<global>
<memory_size>8192</memory_size>
<max_threads>8</max_threads>
</global>
3. Dashboard Optimization
Increase session timeout for better user experience:
# In /etc/wazuh-dashboard/opensearch_dashboards.yml
opensearch_security.session.ttl: 86400000 # 24 hours
Backup and Disaster Recovery
Backing Up Wazuh
Create a backup script:
#!/bin/bash
# backup-wazuh.sh
BACKUP_DIR="/backup/wazuh/$(date +%Y%m%d)"
mkdir -p $BACKUP_DIR
# Backup manager configuration
tar -czf $BACKUP_DIR/wazuh-manager-config.tar.gz /var/ossec/etc/
tar -czf $BACKUP_DIR/wazuh-manager-rules.tar.gz /var/ossec/ruleset/
# Backup indexer data
curl -X PUT "localhost:9200/_snapshot/backup_repo" -H 'Content-Type: application/json' -d '{
"type": "fs",
"settings": {
"location": "'$BACKUP_DIR'/indexer"
}
}'
# Backup certificates
tar -czf $BACKUP_DIR/certificates.tar.gz /etc/wazuh-*/certs/
Monitoring Your Wazuh Installation
Health Checks
Create a monitoring script:
#!/bin/bash
# check-wazuh-health.sh
echo "=== Wazuh Health Check ==="
# Check services
for service in wazuh-manager wazuh-indexer wazuh-dashboard; do
status=$(systemctl is-active $service)
echo "$service: $status"
done
# Check API
api_status=$(curl -s -o /dev/null -w "%{http_code}" -k https://localhost:55000)
echo "API Status: $api_status"
# Check indexer cluster
curl -s -k https://localhost:9200/_cluster/health?pretty
Monitoring XDR, SIEM, and Compliance Effectiveness
1. XDR Performance Metrics
# Monitor threat detection rate
curl -k -u admin:password "https://localhost:9200/wazuh-alerts-*/_search" \
-H "Content-Type: application/json" \
-d '{
"query": {
"range": {
"timestamp": {
"gte": "now-24h"
}
}
},
"aggs": {
"mitre_techniques": {
"terms": {
"field": "rule.mitre.technique.keyword"
}
}
}
}'
2. SIEM Event Processing Metrics
# Check events per second (EPS)
/var/ossec/bin/wazuh-control info | grep "Events processed"
# Monitor queue usage
/var/ossec/bin/agent_control -Q
3. Compliance Score Tracking
# Generate compliance report
/var/ossec/bin/wazuh-control --compliance-report pci-dss > /tmp/pci-compliance.txt
# Check configuration assessment results
curl -k -u admin:password "https://localhost:9200/wazuh-alerts-*/_search" \
-H "Content-Type: application/json" \
-d '{
"query": {
"match": {
"rule.groups": "sca"
}
}
}'
Best Practices for XDR, SIEM, and Compliance
XDR Best Practices
- Threat Intelligence Management
- Update threat feeds daily
- Validate IOCs before implementing
- Create custom feeds for your industry
- Monitor false positive rates
- Response Automation
- Start with low-risk automated responses
- Implement approval workflows for critical actions
- Test responses in isolated environments
- Document all automated actions
- Detection Engineering
- Create detection rules based on your threat model
- Map detections to MITRE ATT&CK
- Continuously tune rules based on false positives
- Share successful detections with the community
SIEM Best Practices
- Log Management Strategy
- Prioritize high-value log sources
- Implement log rotation and retention policies
- Use compression for long-term storage
- Regular log source health checks
- Correlation and Analysis
- Build use case-specific correlation rules
- Create baseline behavior profiles
- Implement anomaly detection thresholds
- Regular review and tuning of rules
- Performance Optimization
- Index only necessary fields
- Use time-based indices
- Implement data tiering (hot, warm, cold)
- Regular maintenance of indices
Compliance Best Practices
- Continuous Compliance Monitoring
- Schedule regular configuration scans
- Automate evidence collection
- Create exception management processes
- Maintain audit trails
- Reporting and Documentation
- Generate regular compliance reports
- Document all remediation efforts
- Maintain evidence for audits
- Create executive dashboards
- Integration with GRC Tools
- Export findings to GRC platforms
- Automate ticket creation for violations
- Track remediation progress
- Maintain compliance metrics
Leveraging OSSEC Knowledge
If you're coming from OSSEC, here are key considerations:
- Rule Migration
- Most OSSEC rules work in Wazuh with minor updates
- Test custom rules with wazuh-logtest
- Update rule IDs to avoid conflicts
- Leverage new Wazuh rule features
- Decoder Updates
- OSSEC decoders need XML schema updates
- Take advantage of dynamic decoders
- Use JSON decoder for modern logs
- Test thoroughly before production
- Active Response Evolution
- OSSEC active responses still work
- New Wazuh integrations available
- Enhanced timeout and throttling options
- Better logging and audit trails
Conclusion
Whether you choose an all-in-one installation for simplicity or a distributed deployment for scalability, Wazuh (remember, that's "WAH-zoo"!) provides a powerful platform that serves as an XDR, SIEM, and compliance monitoring solution all in one.
Understanding the OSSEC Foundation Wazuh's strength comes from building upon OSSEC's proven foundation while adding modern capabilities. This heritage means:
- Stability from 20+ years of HIDS development
- Backward compatibility for existing OSSEC deployments
- Familiar architecture for OSSEC users
- Enhanced features that OSSEC users requested but never received
As we've explored, Wazuh is much more than just a log management tool - it's a comprehensive security platform that:
- As an XDR: Provides unified visibility, advanced threat detection, and automated response across your entire infrastructure
- As a SIEM: Offers robust log collection, correlation, and analysis capabilities with enterprise-grade scalability
- As a Compliance Tool: Ensures continuous compliance monitoring across major frameworks like PCI DSS, GDPR, HIPAA, and more
- As an OSSEC Successor: Maintains compatibility while delivering the modern features security teams need
The key to success with Wazuh is:
- Understand the OSSEC heritage - Leverage existing OSSEC knowledge and documentation
- Start with clear objectives - Define whether XDR, SIEM, or compliance is your primary focus
- Plan your architecture based on your environment size and requirements
- Follow security best practices - change default passwords, use TLS, implement least privilege
- Leverage the platform's full capabilities - Don't just collect logs, use correlation, active response, and compliance features
- Migrate from OSSEC thoughtfully - Test custom rules and decoders before production deployment
- Monitor and tune continuously - Security is not a set-and-forget activity
- Keep Wazuh updated with the latest security patches and rule updates
- Join the community for support, best practices, and threat intelligence sharing
For OSSEC users, Wazuh represents the natural evolution of the platform you trust. For new users, you're benefiting from decades of open-source security development. With this guide, you're ready to deploy Wazuh and start enhancing your security posture across detection, response, and compliance.
Remember that installation is just the beginning - the real value comes from properly configuring rules, alerts, and integrations tailored to your environment and security objectives.
Welcome to the Wazuh community...whether it is your homelab or your enterprise you cannot secure what you don't know... so happy monitoring.
For more information on implementing Wazuh or to join the Wazuh community for support and best practices, visit the official Wazuh documentation and community forums.